Some Key Takeaways from the Q1 Cybersecurity Summary
Malicious acters are stepping up efforts to break into networks and computers.
Many vendors have reported on their Q1 2025 security findings, trends and are giving recommendations. Since I primarily use WatchGuard networking products, I will be providing a summary based on what WatchGuard has been reporting.
WatchGuard is a very diverse vendor offering firewalls, access points, identity management (multifactor authentication), and endpoint protection software. They use threat intelligence data from their firewalls and endpoint protection software to compile their quarterly top security threats reports. On the firewalls the antimalware services (intelligent antivirus and legacy gateway antivirus service), APT (advanced persistent threat) blocker service, IPS (intrusion protection service), and DNSWatch provide most of the data for the report.
Overall Malware Trends
According to the Q1 2025 report, this was the highest level of malware detection per firebox for any reporting quarter thus far. From Q4 2024 to Q1 2025 the average detections per firebox was up over 170%. The types of threats being caught was also very different. The threats detected by APT blocker and IPS service saw double digit decreases but the detections by IntelligentAV service jumped 323%.
This indicates is that that the threats are evolving quickly. These threats were not caught by traditional signature-based antivirus because they had not been seen before. The attackers are using polymorphic coding techniques or cheap and freely available evasion tools.
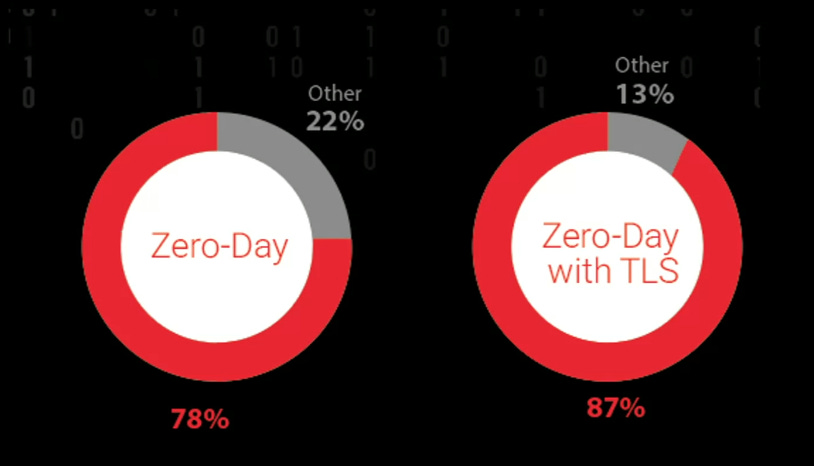
Zero Day Trending
Zero-day malware accounted for nearly 80% of all threats. This means that none of these threats would be caught by signature-based detections. What is even more alarming is that nearly 90% of the zero-day threats were being delivered over TLS encrypted connections. These would primarily be via HTTPS. Today, nearly 97% of all internet traffic is encrypted so this underscores the necessity of dep inspection of HTTPS traffic.
Top Malware
Two new top malware varients stuck out on the list provided. The newest and top malware was a Trojan HTML based email Dropper called Trojan.Agent.FZPI. This was sent as an HTML attachment that looked like an Adobe update web page. It included a password protected zip file that was included on the HTML file. This zip file contained an ISO file with the payload.
The other new malware was a Cashback Dropper that was a malicious version of the adblocker extension called AdBlock Pro for Chrome or Chromium based browsers. Chrome is no longer allowing this browser extension and is blocking its install by default.
Linux malware also continued to be represented with coin miner and botnet malware rounding out the list.
Top Blocked Domains
The domain polyfill.io is still corrupted and web developers should not use it anymore. The domain polyfill.io, is a service that provided JavaScript polyfills for older browsers, has been compromised in a supply chain attack. This attack has affected over 100,000 websites. The vulnerability stems from the acquisition of the polyfill.io domain by a Chinese company, Funnell, which then deliberately compromised the library.
The vast majority of the other top malicious malware domains are crypto miner domains. The type or frameworks of most compromised sites is WordPress. Typically WordPress sites that have not been updated are easily compromised due to vulnerabilities and after being compromised, these are commonly used by malicious actors to spread attacks. The top phishing domain tactic is one that looks like a real MS SharePoint site. It tries to steal credentials by trying to trick users to provide MS credentials to log into it. Having DNS protection is highly affective in protecting these types of attacks.
Delivery Methods
There was a marked drop in PowerShell scripting attacks during the reporting period, but it did not stop the Script category from still being the top category for malware delivery. This was followed by Windows Executables being high as well. Browsers ticked up which could indicate that attackers could be ramping up watering hole or other browser-based attacks.
Protection Tips
Use as many firewall and endpoint detection services as possible to protect networks and endpoints.
Use machine learning (AI) detection. Attackers are utilizing AI to develop and spread malware. It is now possible for attackers to use AI to develop the attack chain and we need to use it to protect against this. This should be used on both for firewall and endpoint
We need to ramp up and defend against malicious attachments in email. It is highly recommended to block .exe, .dll .iso and .link files in emails. These are commonly being used by attackers and these file types are rarely sent for legitimate purposes.