16 Billion Passwords Exposed in the Latest Breach of 2025
Is this the "Mother of all breaches?"
In a technology centric world where a username and password grants access to nearly everything, researchers have just confirmed what could be the largest credential leak ever. This leak, which some have dubbed “The mother of all leaks” contains almost 16 billion login credentials (including those precious usernames and passwords). As part of an ongoing investigation that started at the beginning of the year, the researchers have postulated that the massive password leak is the work of multiple infostealers.
The leaked data includes login info for just about every online service you can think of: Apple, Facebook, Google, GitHub, Telegram, and even government platforms. With 16 billion records floating around, it's safe to say almost no platform or service was left out.
To be very clear – this leak is a compilation of multiple databases that include of both old and recent infostealer logs – often with tokens, cookies, and metadata. The recent logs are all from this year and make up the vast majority of the data and this makes this breach particularly dangerous for organizations lacking multi-factor authentication or strong credential hygiene practices.
Were there breaches at any of these services?
Some media outlets have been misleading regarding this breach. It has been reported that Facebook, Google, and Apple credentials were leaked somehow. While this cannot be completely dismissed, currently it is felt that this is at least somewhat inaccurate.
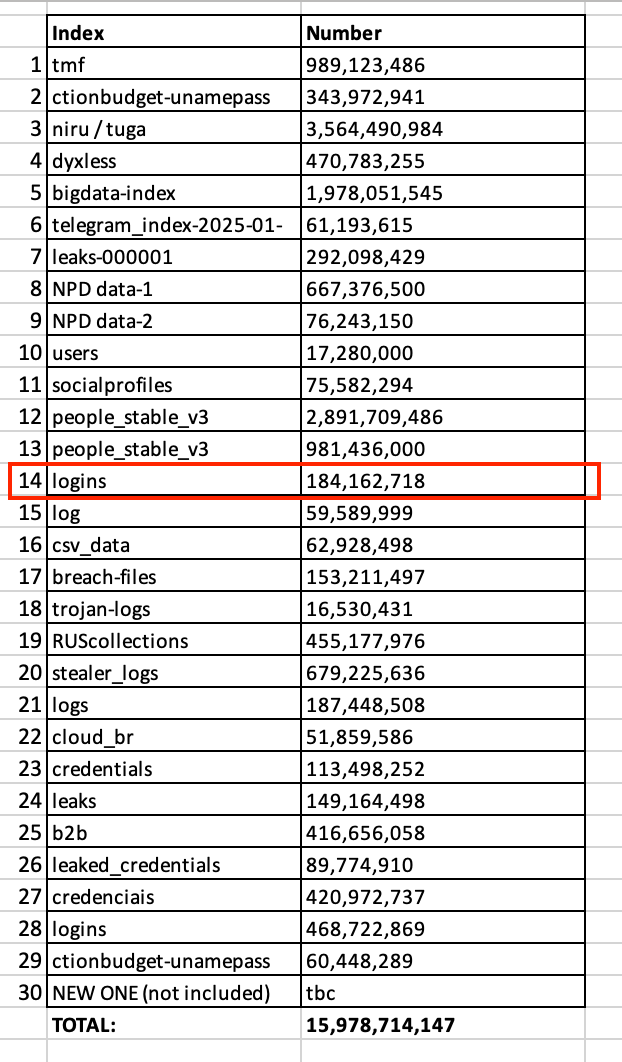
Bob Diachenko, a Cybernews contributor, and the cybersecurity researcher who is behind this discovery of these infostealer lists said when asked directly about the lists “There was no centralized data breach at any of these companies.” Diachenko also indicated all the databases except for one called logins, which contains 184 million credential pairs, are newly gathered as of 2025.
However, since this list was open to the internet, it does not mean that none of the logins were breached and leaked to the dark web.
The format of the lists indicate that their origin is in fact from infostealer activity and this leads researches to believe that these credentials have been gathered from infected computers around the world.
What is an infostealer?
An infostealer, also known as an information stealer, is a type of malware designed to infiltrate a computer system and steal sensitive information. This stolen data is then typically sent to a remote server controlled by cybercriminals. Once they receive the data they can use it for various malicious purposes.
Infostealers are designed to steal a variety of data, including login credentials, financial information, personally identifiable information (PII), and browser data. They can also target emails, chat logs, images, documents, and cryptocurrency wallets. Infostealers are commonly spread through phishing emails, malicious websites, malvertising, infected software, and malicious links.
Infostealers have been hard at work
The infostealer problem has gotten so bad and pervasive that compromised credentials have become one of the most common ways for threat actors to breach networks.
If someone is infected with an infostealer and has a thousand credentials saved in their browser, the infostealer will steal them all and store them in the log. These logs are then uploaded to the threat actor, where the credentials can be used for further attacks or sold on cybercrime marketplaces.
As infostealers have become so abundant and commonly used, threat actors release massive compilations for free on Telegram, Pastebin, and Discord to gain reputation among the cybercrime community or as teasers to paid offerings.
The dangers of this list in particular
The dangers of lists list big being available are that hackers can use this data to launch a variety of attacks. And with newer and more advanced hacking tools this becomes easier every month that goes by. Also, with powerful and freely available AI tools, messaging and list manipulation can happen extremely easily. This will make targeting and attacking easier for cybercriminals. Overall the risks include:
Credential stuffing: Hackers try your login across banking, streaming, shopping, or investment sites. If you reuse passwords, they could gain access to your most sensitive accounts.
Phishing and social engineering: With access to personal details or email accounts, scammers can send convincing fake messages or impersonate you to friends, coworkers, or customer service agents. This can lead to business email compromise.
Identity theft: Stolen credentials can be used to open credit cards, apply for loans, or take over government benefit accounts in your name.
Access to 2FA and backups: If hackers get into your email, they may intercept security codes, password reset links, or even gain access to your cloud storage and documents.
What should you do?
The most important step is to adopt and maintain good cybersecurity habits that you should already be following.
All computers must be protected by a modern next generation antivirus software. These programs not only use signatures but also behavioral analysis and whitelisting to look at everything running on a computer. Both Mac and Windows computers need this protection. So far this year Infostealers have been the leading form of malware on Mac computers.
Change passwords and do not reuse passwords on multiple websites. Only use unique, strong password for every website login you have.
Use a dark web monitoring service to check if you have fallen victim to this or other breaches.
Use a password manager — stop relying on your memory, sticky notes, or the browser’s password manager (which is one of the causes of this problem in the first place!). Let an encrypted vault generate strong passwords for you. This makes it easier to change your password frequently, which is another best practice.
Turn on 2FA — that’s two-factor authentication. It adds a second layer of defense, and it’s free on most platforms. This will help you stay protected if you are hacked, fall for a phishing attack, or install malware. Many password managers will not only store usernames and passwords but your MFA information as well.
As a general rule, you should avoid using SMS texts to receive 2FA codes, as threat actors can conduct SIM-swapping attacks to hijack your phone number and obtain them.
There is a chance your information could be listed in this list of breached accounts. If so, do not panic and stress about it, running around changing all your passwords. Instead, take this opportunity to improve your cybersecurity habits.
And if you use the same password across multiple sites, now is the time to switch to unique ones and turn on MFA. That way, leaks like this become far less dangerous to you. Also, everyone needs to be on alert. Typically, phishing scams tend to spike after big breaches.